Award Winning Technology

Latest Blog Posts
Attacks Stopped by SCIT
SCIT Defends Against Many Attacks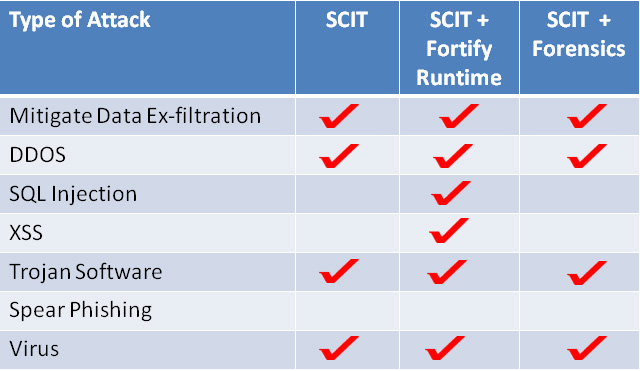
Many cyber attacks are opportunistic and others are targeted. SCIT technology defends against both. For more information about how SCIT disrupts an opportunistic attack click here. How SCIT defends against targeted attacks click here. Examples of attacks disrupted by SCIT are in Table. SCIT complements reactive systems. Combining SCIT with reactive security devices like HP Fortify Runtime and Guidance Software Encase forensics tool mitigates more attacks.




